  |
     
Fraud is not limited to transactions in the "real world"; it also occurs in e-commerce. Many illegal techniques are used by crackers (people who steal or corrupt data) and criminals to capture credit card numbers, social security numbers, passwords, and other personal information. However, there are also many ways to protect oneself from fraud online and keep all personal information private.
Many types of techniques are used by online scammers: spoofing, sniffing, content alteration, and denial.
| Fraud techniques |
| Spoofing | a technique used when a site mimics a legitimate e-business site completely including the site's layouts, fonts, colors, and graphics; the illegal site also registers a similar domain name (e.g. Amazon.com vs. Amazin.com). The fake site functions to steal credit card information or steal business by offering a product at a very low price to influence consumers to buy it and use their credit card (Smith, Speaker, & Thompson 162). |
| Sniffing | used to describe the act of reading a packet of unsecured information as the information travels over a network. This is done by using different sniffing programs that were "originally designed to assit in network error detection" (Smith, Speaker, & Thompson 163). Some crackers watch for transactions to occur to and from certain Internet Provider (IP) addresses. If they find something, they sell the information to criminals or to the company's competitors. |
| Content Alteration | Sniffers intercept bank account numbers to divert payments. Sometimes, they also alter the shipping address for an order. |
| Denial | It is done by conducting a transaction with a business on the Internet, then denying ordering it when the bill is received (Smith, Speaker, & Thompson 163). |
Fraud protection
- Keep a record of purchases online by printing a copy of the order and confirmation number.
- Establish a password that consists of both numbers and letters. Do not use the same password for everything and do not give it to anyone.
- Read the company's private policy. It should state information that will be collected on the site and how it is used.
- Use an Internet browser (such as Microsoft's latest version of Internet Explorer) that complies with set standards for industry security, like Secure Sockets Layer (SSL) or Secure Electronic Transaction (SET) ("Shop Safely Online").
- Before purchasing from a site, check if it is rated by BizRate or Gomez Advisors.
- Before entering a credit card number online, determine if the page is secure.
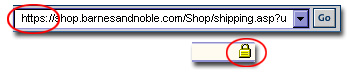 Look for a Uniform Resource Locator (URL) that has "https" rather than "http". Most Web browsers show a small padlock icon along the bottom of the window (Lee 25). Look for a Uniform Resource Locator (URL) that has "https" rather than "http". Most Web browsers show a small padlock icon along the bottom of the window (Lee 25).
- Since there are laws protecting credit card users, it is much safer to use a credit card when ordering rather than a debit card, a check, or money order (Masland).
- Consumers should look for any "real world" contact such as a phone number or address. Pick up the phone and call to see if a live person answers (Sisk: personal interview).
<--Back
|










